Home Lab
Published: 2024-02-12
Intro
Greeting fellow nerds! In this the 2024th year of our lord, Kermit J Frog. I am commited to upskilling on Observability and Kubernetes. To achieve this, I am building out my home lab and using the ways of DevOps.
Technologies
Before I can start building a Kubernetes cluster, I need to build out all the supporting services. The following table lists the hardware and software technology I am using in my lab.
Architecture
I created a few diagrams to help visualize the network.
Physical Network
The physical network is a simple setup with three compute nodes, and a single switch. The following diagram shows the physical network layout.
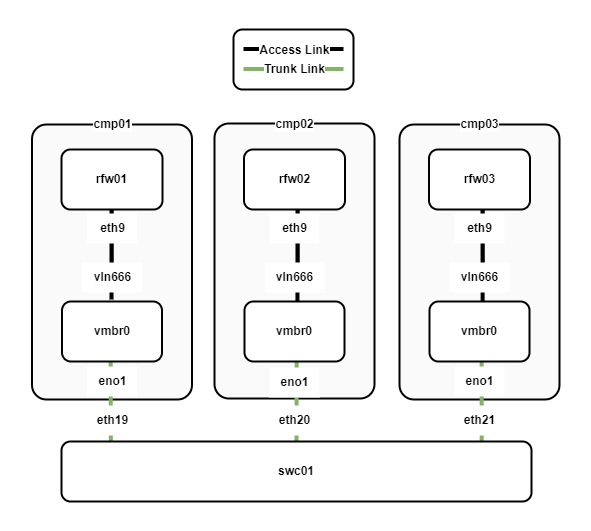
The following points describe the physical network layout:
- Three compute nodes cmp01-03 are running the Proxmox hypervisor and utilise Open vSwitch as the virtual switch.
- The compute nodes connect to swc01 via a trunk link which allows multiple VLANs to be shared between the compute nodes.
- Each compute node has a VyOS virtual router/firewall. The VyOS VMs are configured as the default gateway for all the internal networks.
VLANs
Functions are logically seperated into VLANs. The following diagram shows the VLAN assignment between the VyOS routers and the hypervisor switch.
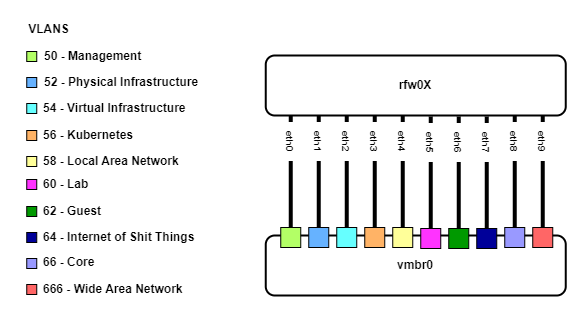
The following points describe the VLAN assignments:
- Three VyOS VMs (rfw01-03) have 10 interfaces, one for each VLAN.
- Each interface connects to the Open vSwitch bridge and is assigned to a VLAN.
Virtual Router Redundancy Protocol (VRRP)
VRRP is used as the first-hop redundancy protocol. The following diagram shows the VRRP configuration between the VyOS routers.
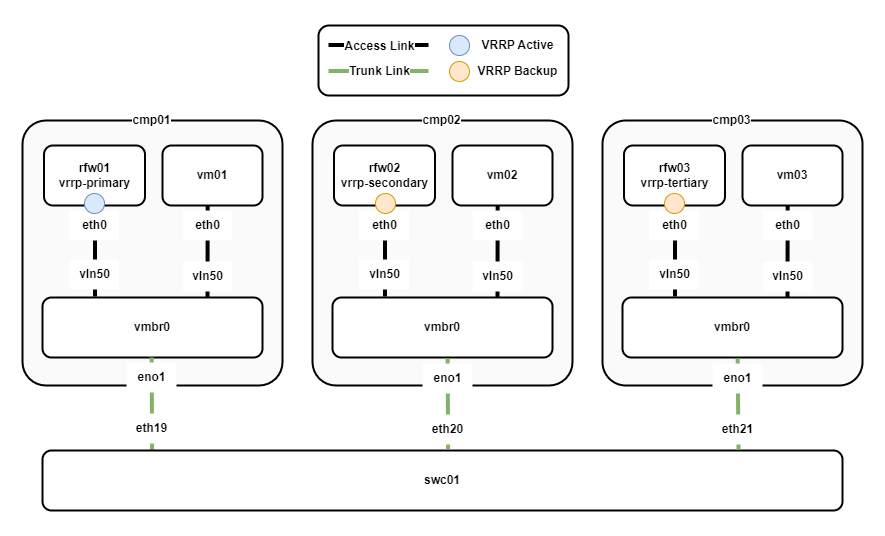
The following points describe the VRRP configuration:
- rfw01 is the active router and rfw02/03 backup routers.
- The VRRP priority of the routers is set so that rfw01 has the highest priority, rfw02 the second highest, and rfw03 the lowest.
- Preempt is enabled, so if rfw01 fails, rfw02 will take over as the active router. When rfw01 comes back online, it will again become the active router.
- Virtual machines vm01-3 use the VRRP virtual IP of the active router as their default gateway.
Routing
The IS-IS routing protocol is used to share routing information between the VyOS routers. The following diagram outlines the routing configuration for both the LAN and WAN.
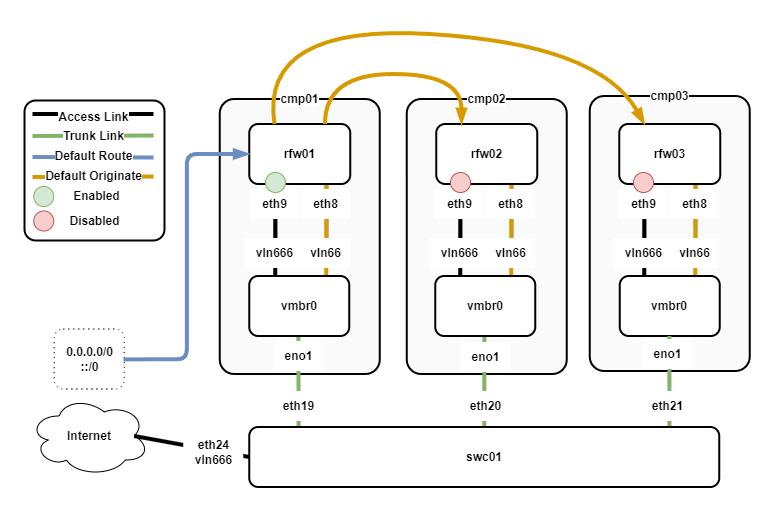
The following points describe the routing configuration:
- rfw01/02/03 have an IS-IS neighbourship over eth8.
- All VyOS routers have eth9 configured to connect WAN, however, only rfw01 has eth9 enabled.
- rfw01 receives the default route from the ISP.
- rfw01 originates the default route for IPv4/6 via IS-IS.
- rfw02/03 receive the default routes from rfw01 via IS-IS.
IPAM
I am running a dual-stack network with IPv4 and IPv6. Each VLAN has a /23 IPv4 CIDR and a /64 IPv6 CIDR. The following table outlines the IPAM for the network.
Physical Infrastructure
The following table lists the addresses for the physical infrastructure.
Virtual Infrastructure
The following table lists the IP addresses for the virtual infrastructure.
Core
The following table lists the IP addresses for the core network.
Loopbacks
The following table lists the loopback IP addresses.
Outro
That's all for now. I will keep updating this post as I progress through the build.
✌️ Peace out nerds. Stay weird! ✌️